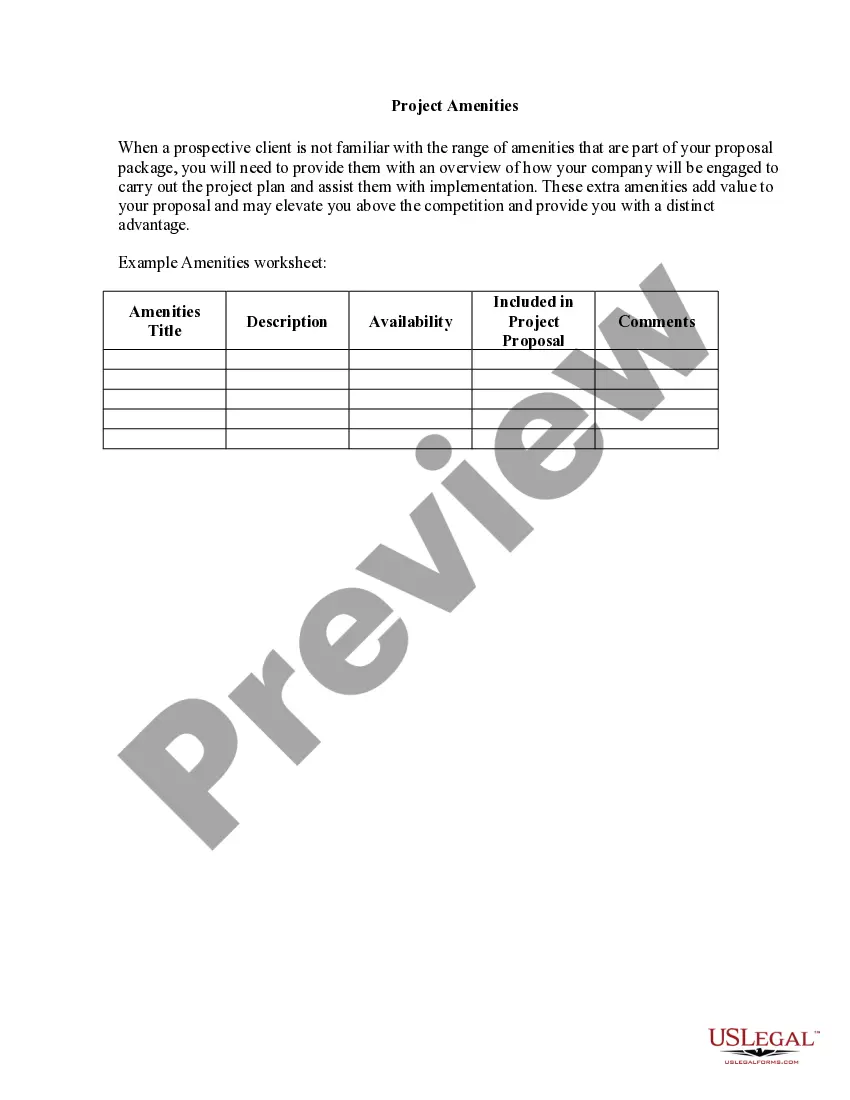
Oregon Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test
Description
How to fill out Ethical Hacking Agreement For External Network Security - Unannounced Penetration Test?
You might spend hours online searching for the legal document template that meets the federal and state requirements you require.
US Legal Forms provides numerous legal forms that are reviewed by professionals.
You can easily obtain or generate the Oregon Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test with my assistance.
If available, utilize the Review button to browse the document template as well. If you wish to find another version of the form, use the Search field to locate the template that meets your requirements and needs.
- If you possess a US Legal Forms account, you can Log In and click on the Obtain button.
- After that, you can complete, modify, generate, or sign the Oregon Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test.
- Every legal document template you purchase is yours indefinitely.
- To have an additional backup of a purchased form, visit the My documents tab and click on the corresponding button.
- If you are using the US Legal Forms website for the first time, follow the simple instructions below.
- First, verify that you have selected the correct document template for the location/city of your choice.
- Check the form description to ensure you have chosen the right form.
Form popularity
FAQ
A pentesting contract should include key elements such as the scope of the test, confidentiality clauses, liability limitations, and payment terms. It must also address the permissions granted for the Oregon Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test, outlining what ethical hackers can access and test. Clear terms regarding the reporting of findings and how they will be shared also prove critical in establishing mutual trust. By clearly defining these components, both parties can engage confidently.
A comprehensive test should include defined goals, methodologies, a clear scope of work, and a timeline. Specifically, for the Oregon Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test, it should detail the systems to be tested, the type of tests to be performed, and any exclusions. Additionally, it should outline reporting requirements for findings and remediation steps. Having these elements in place ensures a thorough and effective testing process.
To engage in a test legally, an ethical hacker needs explicit authorization from the organization being tested. This authorization is often formalized through an Oregon Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test. The agreement should outline the scope, objectives, and limitations of the test, ensuring both parties understand their responsibilities. Without proper consent, ethical hacking could be considered illegal and unethical.
Ethical hacking involves simulating cyberattacks to identify vulnerabilities without malicious intent. In contrast, testing commonly refers to assessing systems and applications for various types of weaknesses. Under the Oregon Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test, ethical hacking emphasizes security measures, while testing broadly encompasses various quality assurance processes. Understanding this distinction helps businesses choose the right approach for their security needs.
An effective pentest report under the Oregon Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test should include an executive summary, detailed findings, recommendations for remediation, and a scope of the test. It is important to articulate both vulnerabilities and their potential impacts clearly. Additionally, including a timeline of the testing process adds transparency and aids in understanding. Make sure to utilize a structured format to improve readability and impact.
No, testing is not illegal when done under the right conditions. However, conducting tests without permission can lead to significant legal consequences. Engaging in an Oregon Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test ensures that all parties understand the expectations and limits. By following legal guidelines, ethical hackers can perform their work safely and effectively.
Absolutely, ethical hacking is legal when conducted with proper authorization. This usually involves a signed Oregon Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test, which outlines the scope and boundaries of the testing. When ethical hackers obtain consent from the organization, they contribute to improving security legally and responsibly. This practice fosters trust between companies and their cybersecurity teams.
Yes, ethical hackers perform various types of testing to ensure systems are secure. They conduct assessments, such as those outlined in the Oregon Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test, which helps reveal weaknesses in a network. By simulating attacks, they provide valuable insights that help organizations safeguard their data. Their testing ultimately benefits everyone involved by reducing risks.
Yes, a pentester is considered a type of hacker, but with an ethical focus. Unlike malicious hackers, pentesters operate under the guidelines of an Oregon Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test. Their goal is to identify and fix vulnerabilities within a system, enhancing overall security. By working within legal boundaries, they contribute positively to network safety.
In this context, testing refers to the practice of evaluating the security of external networks through penetration testing. The Oregon Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test describes how ethical hackers simulate attacks to identify vulnerabilities. This proactive approach helps organizations strengthen their defenses and protect sensitive information. Effective testing is essential for maintaining cybersecurity and building trust with clients.