Iowa Authorization for Use and / or Disclosure of Protected Health Information
Description
How to fill out Authorization For Use And / Or Disclosure Of Protected Health Information?
US Legal Forms - one of the largest collections of authentic documents in the United States - offers a variety of legitimate document templates that you can download or print.
By using the website, you can discover thousands of forms for business and personal needs, organized by categories, states, or keywords.
You can find the latest versions of documents like the Iowa Authorization for Use and/or Disclosure of Protected Health Information in moments.
Check the form's description to confirm that you have chosen the right document.
If the form does not meet your needs, use the Search field at the top of the screen to find one that does.
- If you already have a subscription, Log In and access the Iowa Authorization for Use and/or Disclosure of Protected Health Information from the US Legal Forms collection.
- The Download button will appear on each document you view.
- You can access all previously downloaded documents from the My documents section of your account.
- If you are using US Legal Forms for the first time, here are simple steps to get started.
- Make sure you have selected the correct form for your city/region.
- Review the form's content by clicking the Review button.
Form popularity
FAQ
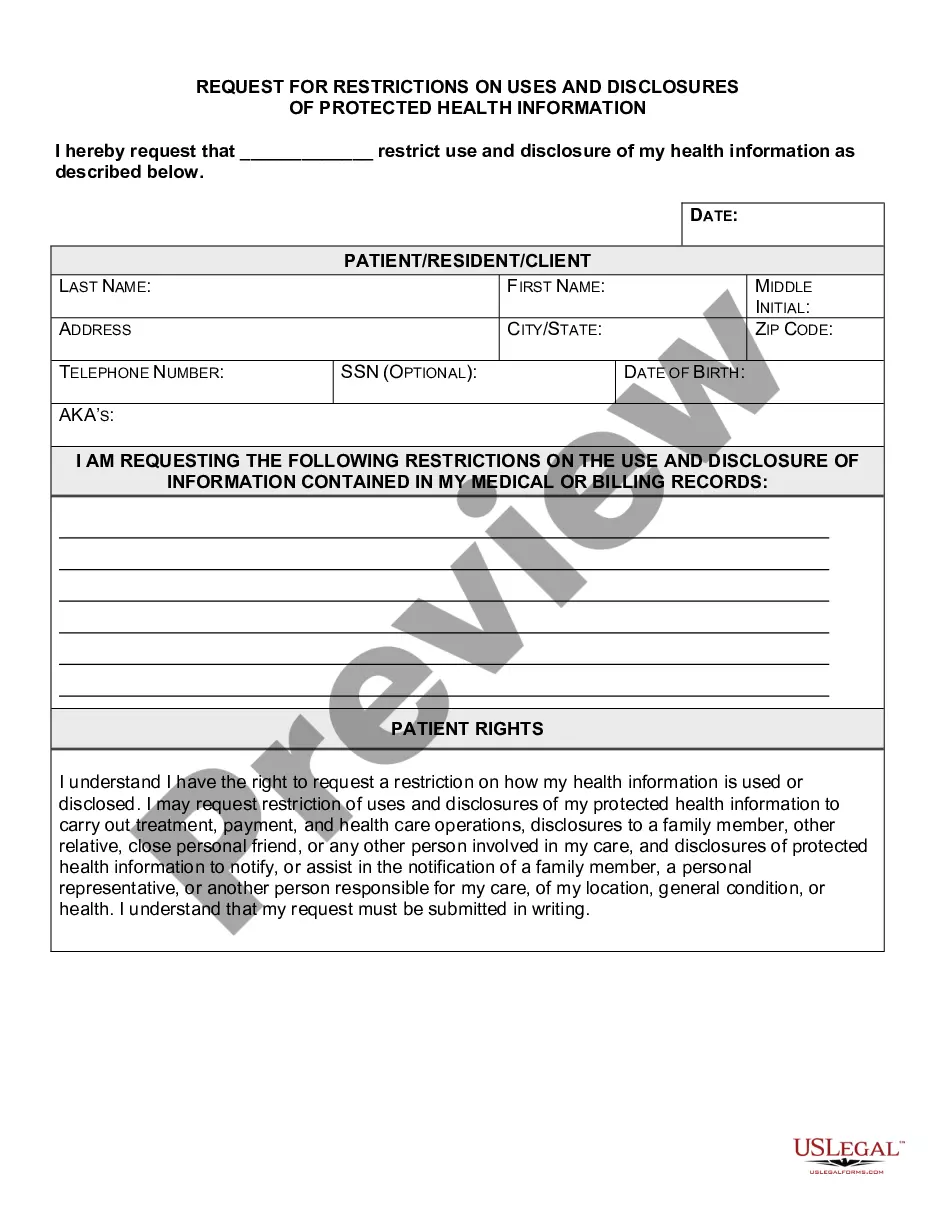
You must obtain authorization from an individual before disclosing their protected health information in various situations. For instance, any time you intend to share health data for purposes beyond treatment, payment, or healthcare operations, you need a valid Iowa Authorization for Use and / or Disclosure of Protected Health Information. This process ensures that individuals maintain control over their sensitive information, fostering trust and transparency. Using platforms like US Legal Forms can simplify the creation of these authorization documents, making compliance straightforward and efficient.
You may file a Security Rule complaint electronically via the OCR Complaint Portal, or using our Health Information Privacy Complaint Package - PDF. If you mail or fax the complaint, be sure to send it to the appropriate OCR regional office based on where the alleged violation took place.
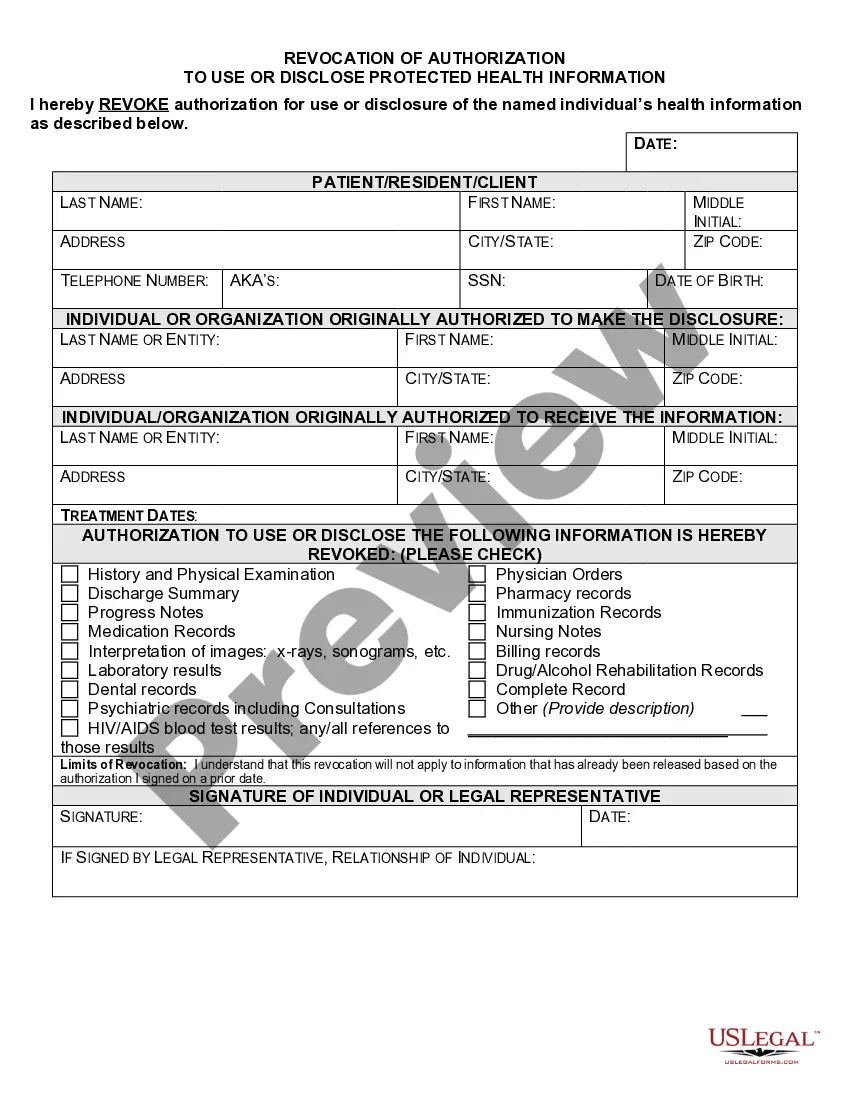
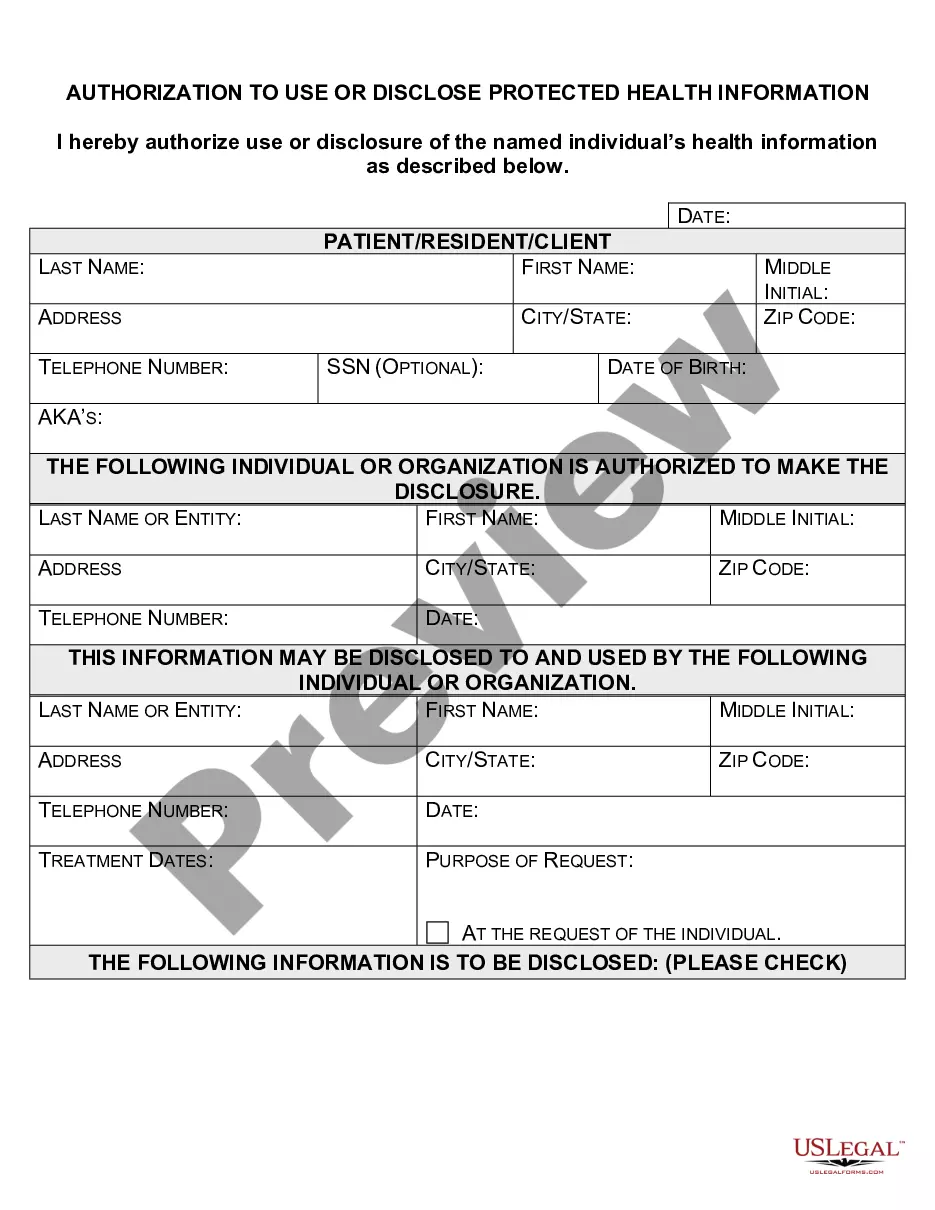
This form is used to release your protected health information as required by federal and state privacy laws. Your authorization allows the Health Plan (your health insurance carrier or HMO) to release your protected health information to a person or organization that you choose.
An authorization must specify a number of elements, including a description of the protected health information to be used and disclosed, the person authorized to make the use or disclosure, the person to whom the covered entity may make the disclosure, an expiration date, and, in some cases, the purpose for which the
Most Common HIPAA Violation Examples1) Lack of Encryption.2) Getting Hacked OR Phished.3) Unauthorized Access.4) Loss or Theft of Devices.5) Sharing Information.6) Disposal of PHI.7) Accessing PHI from Unsecured Location.
Filing a Complaint If you believe that a HIPAA-covered entity or its business associate violated your (or someone else's) health information privacy rights or committed another violation of the Privacy, Security, or Breach Notification Rules, you may file a complaint with the Office for Civil Rights (OCR).
Valid HIPAA Authorizations: A ChecklistNo Compound Authorizations. The authorization may not be combined with any other document such as a consent for treatment.Core Elements.Required Statements.Marketing or Sale of PHI.Completed in Full.Written in Plain Language.Give the Patient a Copy.Retain the Authorization.
You can send a complaint anonymously and explain in the letter or email why you do not want to disclose your identity. If you can provide evidence of HIPAA being violated, your HIPAA Officer should investigate and take action.
Handling HIPAA Breaches: Investigating, Mitigating and ReportingStop the breach.Contact the privacy officer.Respond promptly.Investigate appropriately.Mitigate the effects of the breach.Correct the breach.Impose sanctions.Determine if the breach must be reported to the individual and HHS.More items...?
The core elements of a valid authorization include:A meaningful description of the information to be disclosed.The name of the individual or the name of the person authorized to make the requested disclosure.The name or other identification of the recipient of the information.More items...