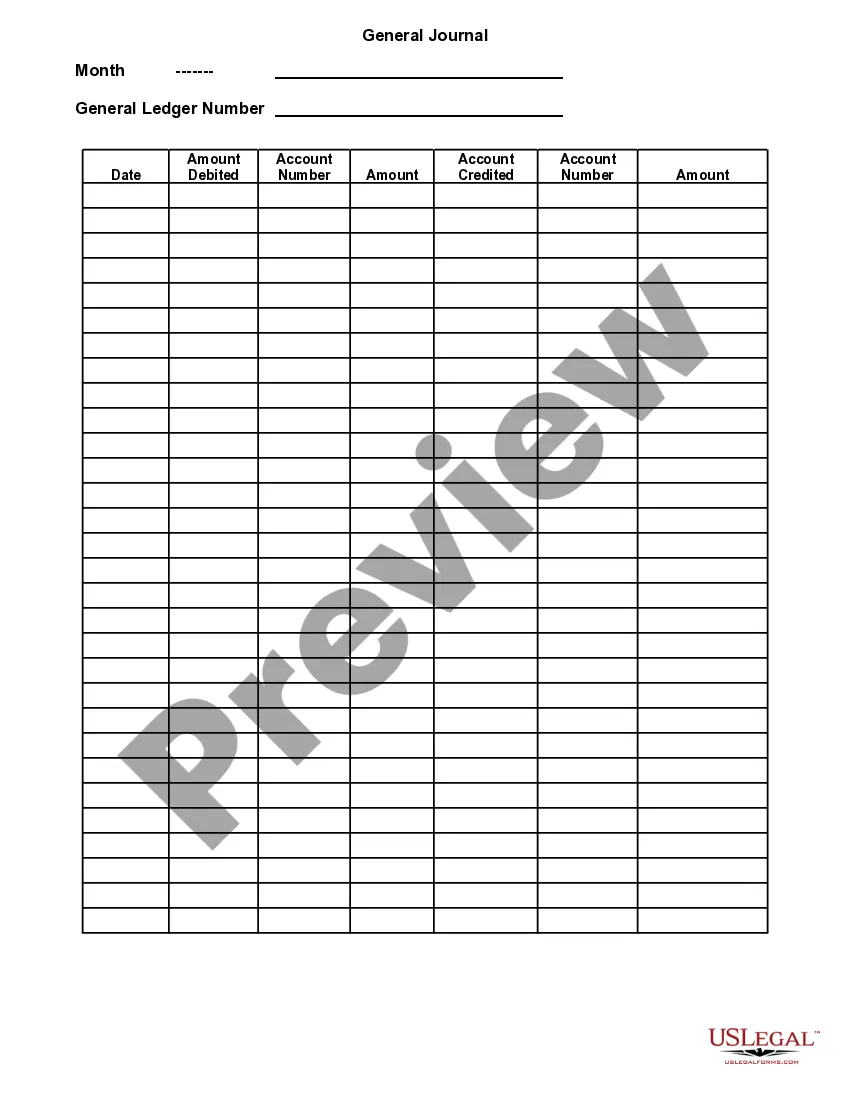
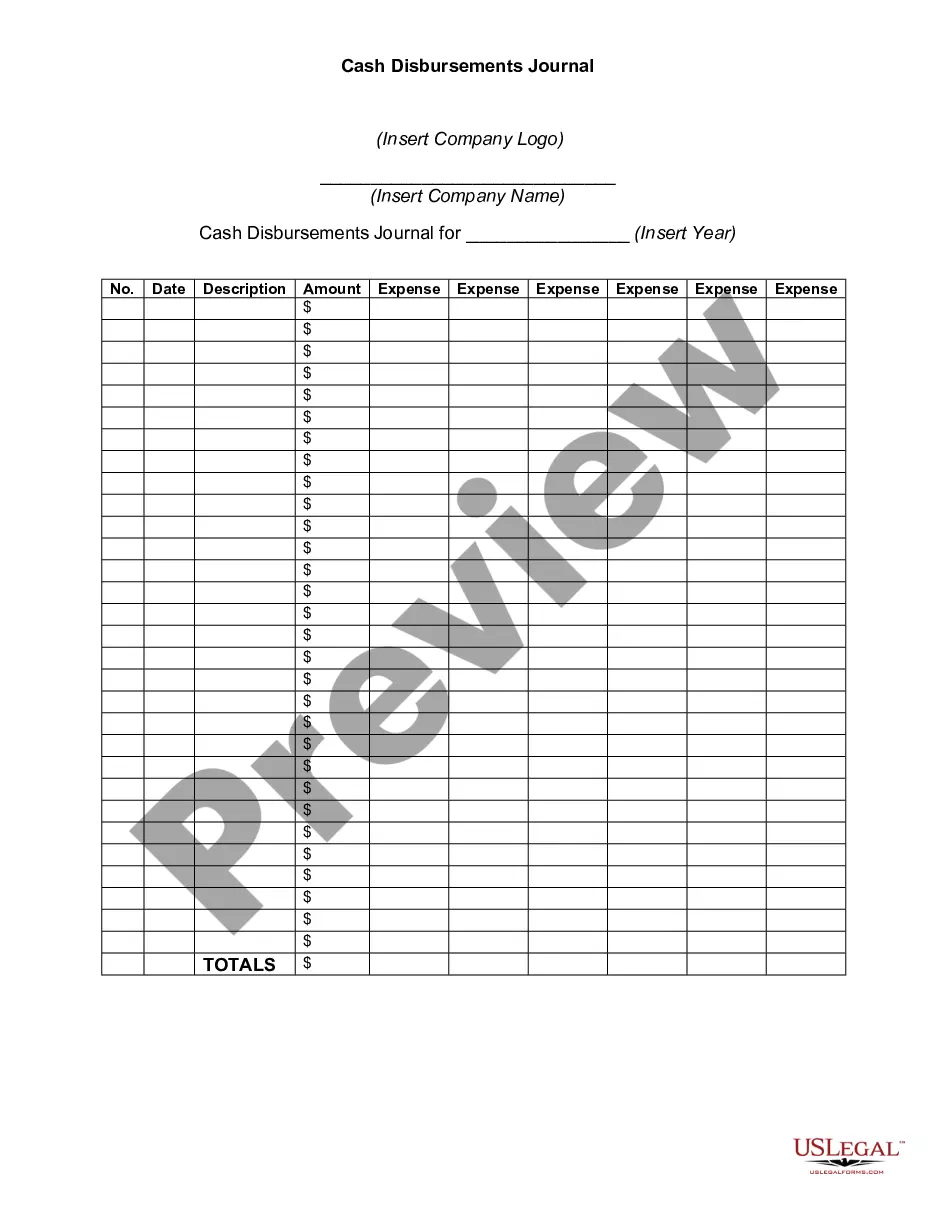
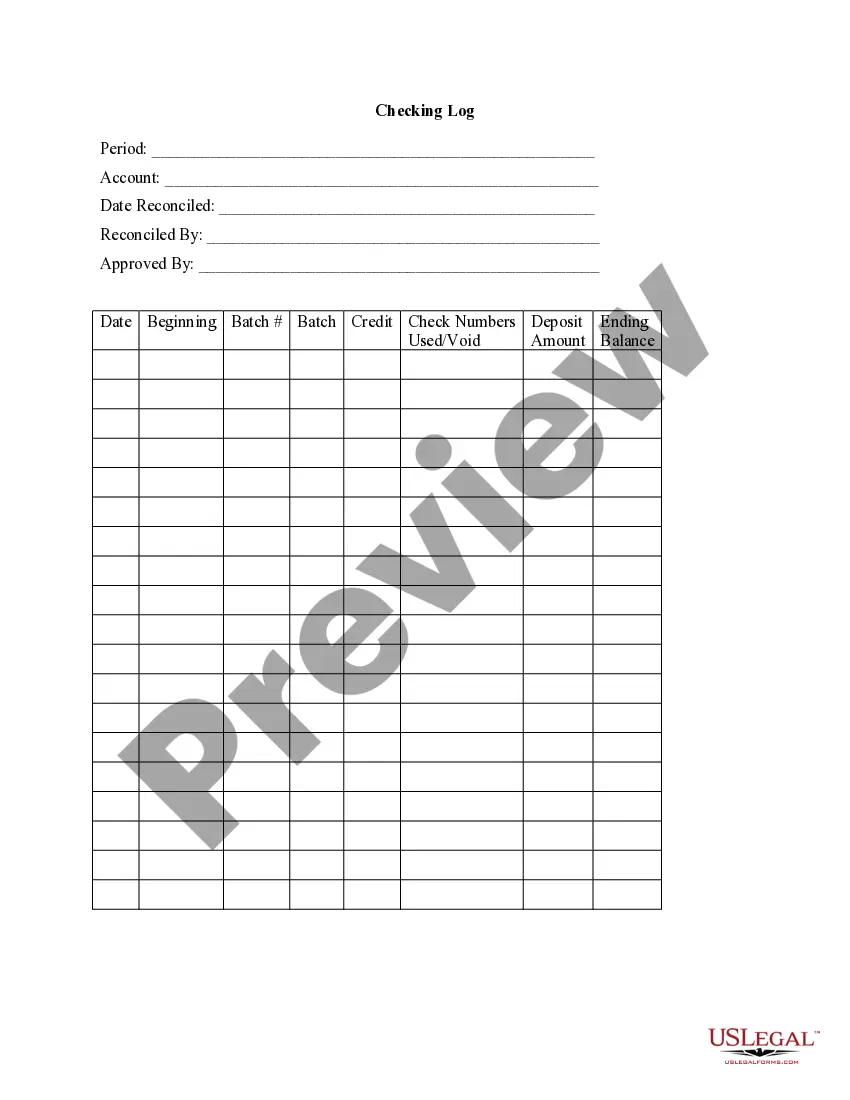
Checking Logs is the process of monitoring system activity and events by examining log files. Logs are generated by applications, services, or operating systems for a variety of purposes, including tracking user behavior, troubleshooting errors, and auditing security. Logs can be checked manually or through the use of automated analysis tools. There are four main types of Checking Logs: 1. System Logs: These logs capture system-level events such as system startup and shutdown, application and service errors, and system resource usage. 2. Application Logs: These logs record the activities of applications, such as user logins and usage of the application’s features. 3. Security Logs: These logs track events that are related to security, such as failed login attempts, firewall breaches, and suspicious user activity. 4. Access Logs: These logs capture user activity on the system, including the time and date of each request, the type of request, and the name of the user who made the request.
Checking Logs
Description
Get your form ready online
Our built-in tools help you complete, sign, share, and store your documents in one place.
Make edits, fill in missing information, and update formatting in US Legal Forms—just like you would in MS Word.
Download a copy, print it, send it by email, or mail it via USPS—whatever works best for your next step.
Sign and collect signatures with our SignNow integration. Send to multiple recipients, set reminders, and more. Go Premium to unlock E-Sign.
If this form requires notarization, complete it online through a secure video call—no need to meet a notary in person or wait for an appointment.
We protect your documents and personal data by following strict security and privacy standards.
Make edits, fill in missing information, and update formatting in US Legal Forms—just like you would in MS Word.

Download a copy, print it, send it by email, or mail it via USPS—whatever works best for your next step.
Sign and collect signatures with our SignNow integration. Send to multiple recipients, set reminders, and more. Go Premium to unlock E-Sign.
If this form requires notarization, complete it online through a secure video call—no need to meet a notary in person or wait for an appointment.
We protect your documents and personal data by following strict security and privacy standards.
Looking for another form?
How to fill out Checking Logs?
How much time and resources do you usually spend on composing official documentation? There’s a better way to get such forms than hiring legal specialists or spending hours searching the web for an appropriate blank. US Legal Forms is the premier online library that provides professionally drafted and verified state-specific legal documents for any purpose, including the Checking Logs.
To acquire and prepare an appropriate Checking Logs blank, follow these simple steps:
- Look through the form content to ensure it meets your state regulations. To do so, check the form description or utilize the Preview option.
- In case your legal template doesn’t satisfy your needs, locate another one using the search bar at the top of the page.
- If you are already registered with our service, log in and download the Checking Logs. Otherwise, proceed to the next steps.
- Click Buy now once you find the correct blank. Opt for the subscription plan that suits you best to access our library’s full service.
- Create an account and pay for your subscription. You can make a transaction with your credit card or via PayPal - our service is totally secure for that.
- Download your Checking Logs on your device and complete it on a printed-out hard copy or electronically.
Another benefit of our service is that you can access previously downloaded documents that you safely keep in your profile in the My Forms tab. Obtain them anytime and re-complete your paperwork as often as you need.
Save time and effort completing legal paperwork with US Legal Forms, one of the most reliable web solutions. Sign up for us today!
Form popularity
FAQ
Thanks to its multiple purposes, log analysis is a critical part of log management. It helps with monitoring and alerting, measuring productivity, security incident response, governmental compliance, and it's useful even in cyber-forensics.
System log - system logs record events that occur within the operating system itself, such as driver errors during start-up, sign-in and sign-out events and other activities.
View the Windows Setup event logs Start the Event Viewer, expand the Windows Logs node, and then click System. In the Actions pane, click Open Saved Log and then locate the Setup. etl file. By default, this file is available in the %WINDIR%\Panther directory. The log file contents appear in the Event Viewer.
Press the Windows key + R on your keyboard to open the run window. In the run dialog box, type in eventvwr and click OK. In the Event Viewer window, expand the Windows Logs menu. Under the Windows Logs menu, you'll notice different categories of event logs?application, security, setup, system, and forwarded events.
Many log files are recorded in plain-text form, which means you can use a program like Notepad or Microsoft Office to open and view a server log file.
Most web servers generate a log file in the Common Log Format (CLF) for every HTTP request. Each log entry contains detailed information about the request, including: the IP address of the device; the date and time of the request; the name and location of the requested file; and the file size.
To check for error logs, follow these steps: Check the log files for error messages. Examine errlog. log first. If indicated, check optional log files for error messages. Identify the errors associated with your problem.