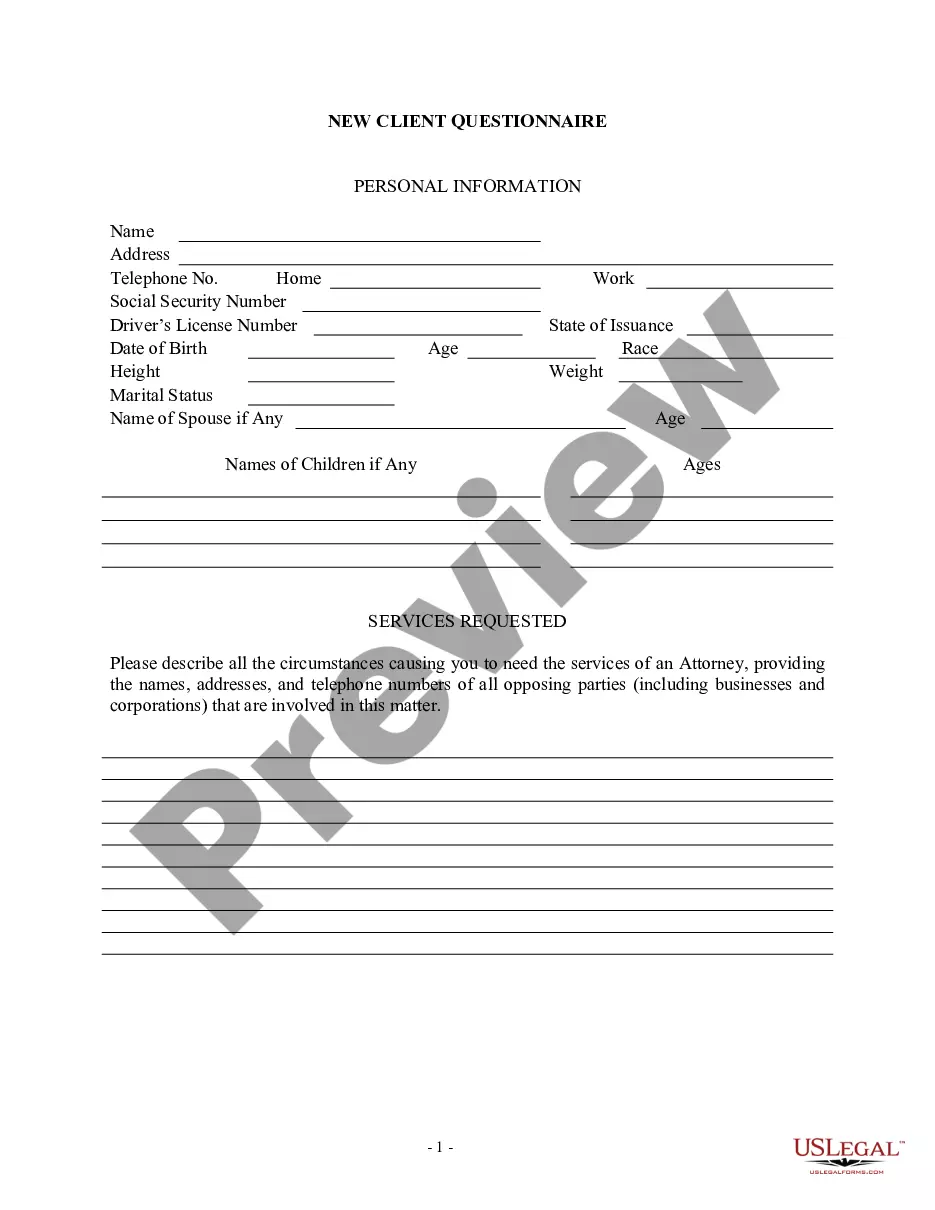
South Dakota Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test
Description
How to fill out Ethical Hacking Agreement For External Network Security - Unannounced Penetration Test?
Selecting the appropriate authorized document template can be quite a challenge. Naturally, there are numerous templates available online, but how can you find the legal document you require? Utilize the US Legal Forms website. The service offers thousands of templates, including the South Dakota Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test, that can be used for both business and personal purposes. All the forms are checked by experts and comply with state and federal regulations.
If you are already registered, Log In to your account and click on the Download button to obtain the South Dakota Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test. Use your account to access the legal forms you have previously purchased. Visit the My documents tab in your account and retrieve another copy of the document you need.
If you are a new user of US Legal Forms, here are simple instructions you can follow: First, ensure you have selected the correct document for your city/region. You can review the form using the Review button and examine the form description to ensure it is the correct one for you. If the document does not meet your needs, utilize the Search area to find the appropriate form. When you are confident that the form is correct, select the Purchase now button to acquire the document. Choose the payment option you prefer and enter the required information. Create your account and pay for the transaction using your PayPal account or Visa or Mastercard. Select the file format and download the legal document template for your product. Complete, modify, and print and sign the received South Dakota Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test.
US Legal Forms is the premier repository of legal documents where you can find a wide variety of document templates. Use the service to acquire properly crafted papers that comply with state requirements.
- Select the appropriate document template.
- Ensure compliance with state regulations.
- Utilize the review and search features.
- Confirm the document's suitability.
- Initiate the purchase process with payment.
- Download and print the document.
Form popularity
FAQ
Legally engaging in a test requires clear documentation, primarily through agreements like the South Dakota Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test. This documentation should outline the scope, permissions, and limitations of the hacking process. Additionally, ethical hackers must ensure they comply with all relevant laws and company policies to maintain legal and ethical standing.
To become an ethical hacker, one must possess a strong understanding of networking, programming, and security principles. Additionally, certifications such as Certified Ethical Hacker (CEH) can enhance credibility and skill proficiency. The South Dakota Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test can become a valuable tool for ethical hackers, helping them formalize their engagement with organizations while demonstrating their expertise.
An ethical hacker can begin the testing process after obtaining explicit authorization through documentation, like the South Dakota Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test. This agreement outlines the scope, timeline, and specific parameters for testing. Having this clarity prevents misunderstandings and ensures all parties are on the same page regarding the testing process.
When engaging in the South Dakota Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test, ethical and legal considerations are paramount. Ethical hackers must secure permission from relevant stakeholders and strictly adhere to laws and agreements in place. Additionally, they should respect privacy, avoid data theft, and ensure that testing does not disrupt services.
Ethical hacking refers to the authorized practice of probing systems for vulnerabilities, while testing often involves a broader evaluation of security measures. In the context of the South Dakota Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test, ethical hacking specifically targets known vulnerabilities to assess and improve overall network security. It's vital to recognize that ethical hacking is structured and sanctioned, ensuring no harm comes to the system.
Testing, in this context, refers to evaluating the security of an external network through ethical hacking practices. The aim is to identify vulnerabilities and security flaws before they can be exploited by malicious parties. Under the South Dakota Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test, testing is conducted transparently and ethically. This preventive measure ultimately helps safeguard your network and sensitive information.
Typically, a testing agreement consists of three main sections: the scope of services, confidentiality agreements, and liability limitations. The scope outlines what will be tested under the South Dakota Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test. The confidentiality agreement ensures that all sensitive data is handled responsibly, while liability limitations protect both parties from unforeseen issues. These sections work together to create a comprehensive and secure agreement.
State and federal laws regarding testing vary but generally focus on privacy and data protection. For instance, laws like the Computer Fraud and Abuse Act set the groundwork for lawful hacking practices under a South Dakota Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test. Familiarizing yourself with these regulations is essential for legal compliance. Always consult legal expertise before conducting any testing.
A test agreement is a formal document that outlines the terms under which ethical hacking tests will be conducted. It includes the expectations, scope, and legal protections of both parties involved in the South Dakota Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test. By clearly defining responsibilities and limits, this agreement ensures a smooth testing process. Having a proper test agreement safeguards against potential risks.
A test contract should include several key documents to ensure clarity and security. You will want to include the South Dakota Ethical Hacking Agreement for External Network Security - Unannounced Penetration Test details, a non-disclosure agreement, and any relevant compliance requirements. Incorporating these documents minimizes misunderstandings and sets clear expectations for both parties. They serve to protect sensitive information and outline the scope of the testing.