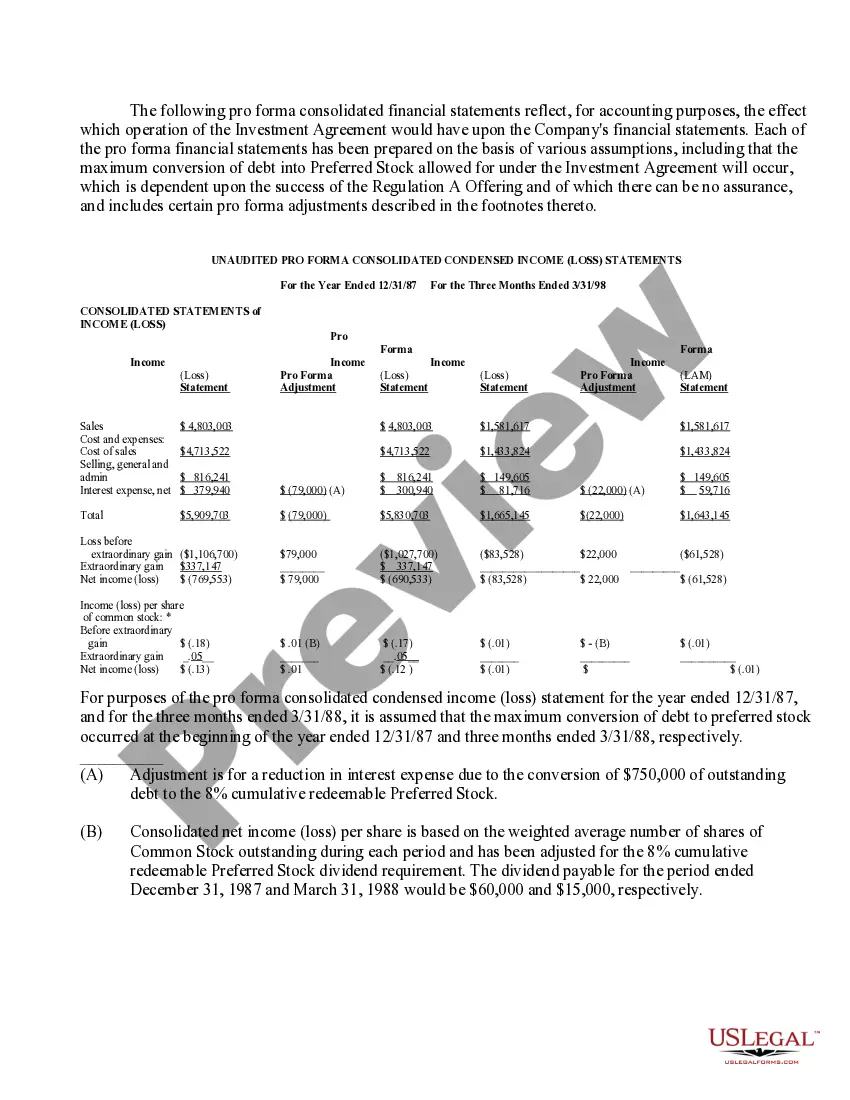
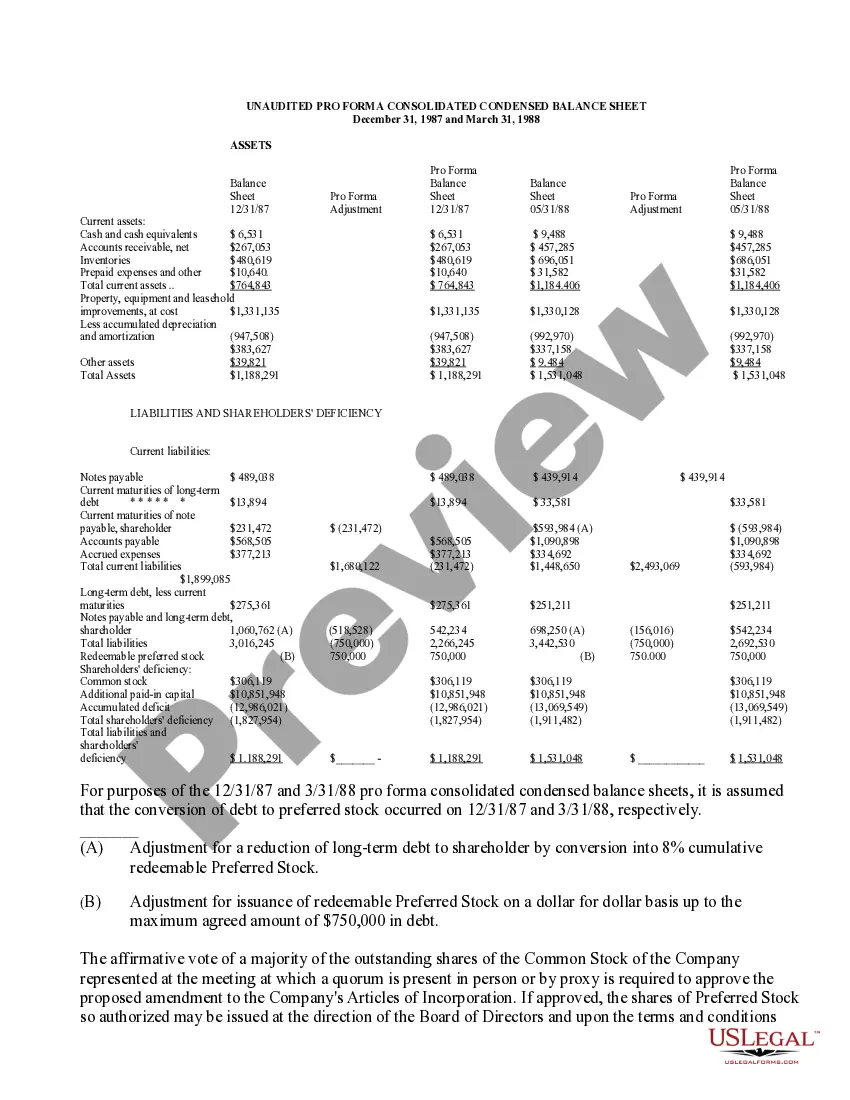
Authorization Stock With Aws
Description
How to fill out Approval Of Authorization Of Preferred Stock?
It’s well-known that you can’t become a legal authority instantly, nor can you understand how to swiftly create Authorization Stock With Aws without a specific skill set. Assembling legal documents is a lengthy process that necessitates specialized training and expertise. So, why not entrust the creation of the Authorization Stock With Aws to the experts.
With US Legal Forms, one of the most extensive legal template collections, you can access everything from court documents to templates for internal business communication. We recognize how crucial compliance and adherence to federal and state regulations are. That’s why, on our platform, all forms are location-specific and current.
Here’s how to get started with our platform and acquire the document you require in just a few minutes.
You can access your documents again from the My documents tab at any moment. If you’re a returning customer, you can simply Log In and find and download the template from the same tab.
Regardless of the reason for your documents—whether financial and legal, or personal—our platform has you covered. Try US Legal Forms today!
- Find the form you need by utilizing the search bar at the top of the page.
- Preview it (if this option is available) and review the accompanying description to see if Authorization Stock With Aws is what you’re looking for.
- Start your search again if you require a different form.
- Create a free account and choose a subscription option to purchase the form.
- Select Buy now. Once the payment is completed, you can download the Authorization Stock With Aws, fill it out, print it, and send it or mail it to the specified individuals or entities.
Form popularity
FAQ
Authorization: determines what an identity can access within a system once it's been authenticated to it. An example of this would be an identity's permissions to access specific AWS services. Access control: the method and process of how access is granted to a secure resource. An example, multi-factor authentication.
During authorization, AWS uses values from the request context to check for policies that apply to the request. It then uses the policies to determine whether to allow or deny the request. Most policies are stored in AWS as JSON documents and specify the permissions for principal entities.
If you add an AWS account to the organization or an OU that has access to a resource share, then that new member account automatically gets access to the resource share. The administrator of the account you shared with can then grant individual principals in that account access to the resources in that share.
Amazon Verified Permissions is a scalable, fine-grained permissions management and authorization service for custom applications built by you. Verified Permissions enables your developers to build secure applications faster by externalizing authorization and centralizing policy management and administration.
Authentication identifies and verifies who you are. Authorization determines what an identity can access within a system once it has been authenticated to it.