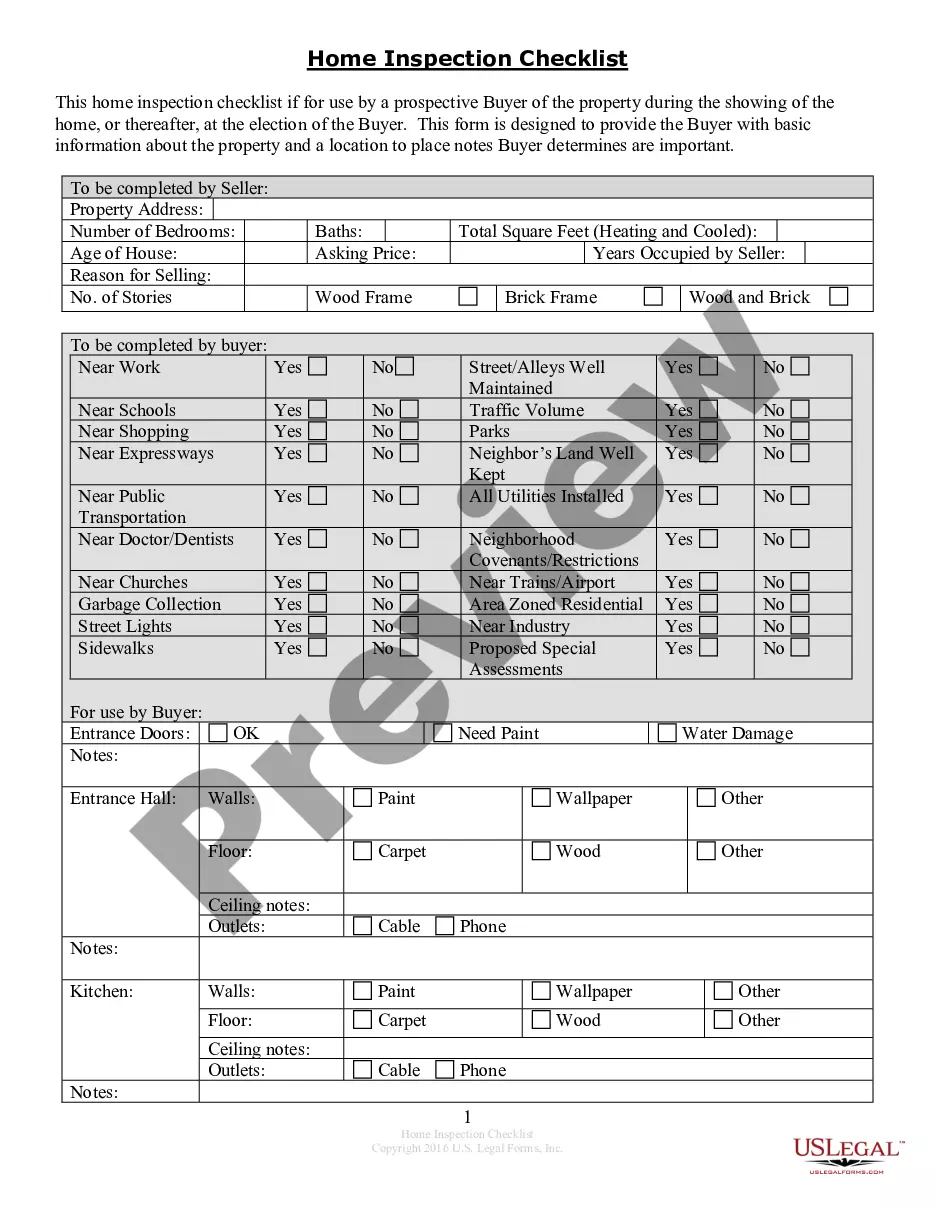
This document is an important policy for a company that relies on its information assets and computer resources to conduct and support its business operations with its customers, employees and suppliers. It seeks to protect business development information, manufacturing and operation information, software and product development, and data security.
Utah Employee Policy for Information Security
Description
How to fill out Employee Policy For Information Security?
It is possible to spend time on-line attempting to find the legal record web template which fits the federal and state needs you require. US Legal Forms supplies thousands of legal varieties that are examined by experts. It is possible to down load or print out the Utah Employee Policy for Information Security from my assistance.
If you already have a US Legal Forms bank account, it is possible to log in and click on the Down load option. Next, it is possible to comprehensive, revise, print out, or indicator the Utah Employee Policy for Information Security. Every single legal record web template you purchase is the one you have for a long time. To get another duplicate of the obtained form, check out the My Forms tab and click on the related option.
Should you use the US Legal Forms web site for the first time, adhere to the easy directions below:
- First, make sure that you have chosen the best record web template for the county/town of your choice. Look at the form information to ensure you have selected the appropriate form. If readily available, utilize the Preview option to check from the record web template at the same time.
- In order to locate another edition of the form, utilize the Search discipline to discover the web template that fits your needs and needs.
- Once you have found the web template you want, click Acquire now to proceed.
- Pick the costs strategy you want, type your references, and sign up for an account on US Legal Forms.
- Comprehensive the financial transaction. You can utilize your Visa or Mastercard or PayPal bank account to cover the legal form.
- Pick the formatting of the record and down load it to your product.
- Make changes to your record if required. It is possible to comprehensive, revise and indicator and print out Utah Employee Policy for Information Security.
Down load and print out thousands of record web templates using the US Legal Forms Internet site, that provides the greatest selection of legal varieties. Use professional and status-distinct web templates to tackle your company or person requires.
Form popularity
FAQ
?Preserving authorized restrictions on information access and disclosure, including means for protecting personal privacy and proprietary information.?
What is an Information Security Policy? Information security (infosec) refers to policies, processes, and tools designed and deployed to protect sensitive business information and data assets from unauthorised access.
Section 7: Threats Part of the reason information security policies exist is to mitigate the risk of information security threats to the organization. By associating policies with threats from the GLBA risk assessment, it is easy to demonstrate how policies are effectively reducing the risk of those threats.
An ISP provides your employees with clear guidelines for handling sensitive information within your organization. This may help improve general cybersecurity awareness and decrease the number of unintentional insider threats.
Confidentiality ? Only authenticated and authorized individuals can access data and information assets. Integrity ? Data should be intact, accurate and complete, and IT systems must be kept operational. Availability ? Users should be able to access information or systems when needed.
The U.S. Department of Defense has promulgated the Five Pillars of Information Assurance model that includes the protection of confidentiality, integrity, availability, authenticity, and non-repudiation of user data.
An information security policy should address all data, programs, systems, facilities, other tech infrastructure, users of technology and third parties in a given organization, without exception.
A: Three types of security policies in common use are program policies, issue-specific policies, and system-specific policies.