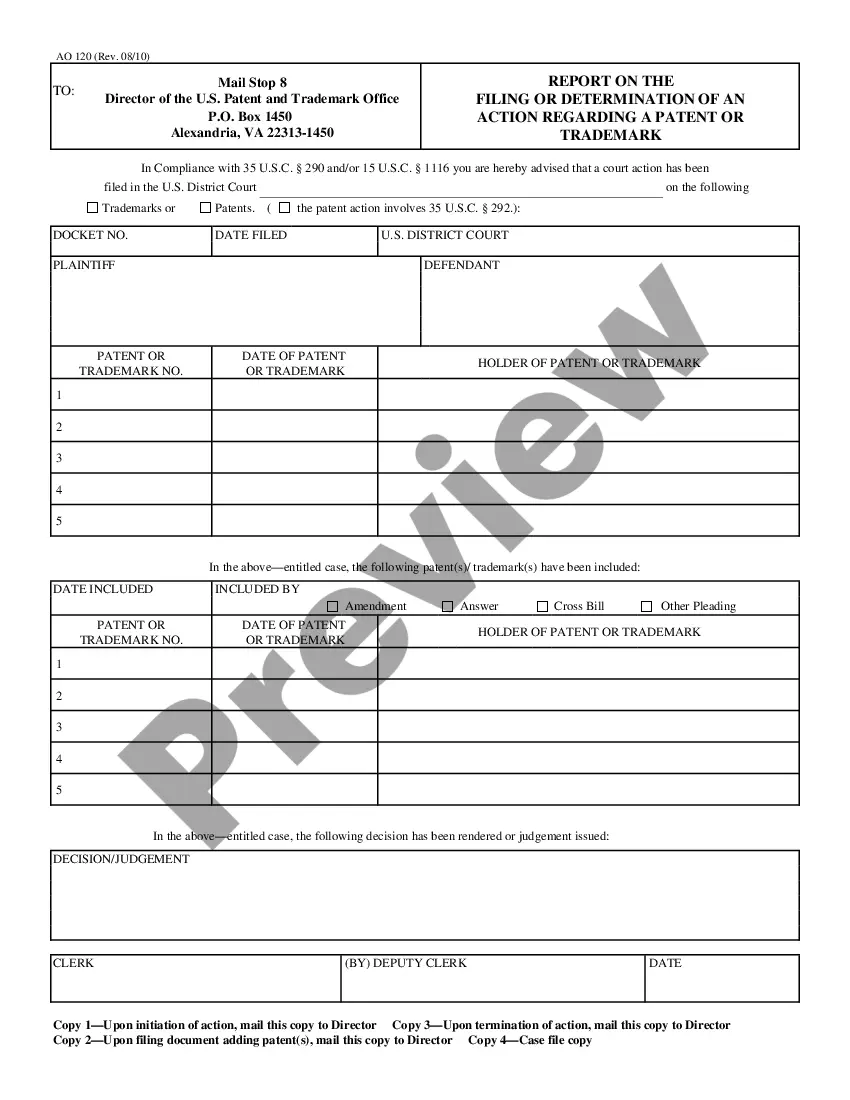
Employee Key Holder Agreement Form In North Carolina
Description
Form popularity
FAQ
Key-holder Agreement Form The key provided is not to be loaned or otherwise to leave the care of the keyholder named above. Under no circumstances is the key to be duplicated. Loss of the key is to be reported immediately to registered manager within PICO. The keyholder will be responsible for the security of the key.
Secret key agreement is the procedure for agreeing on a secret key by exchanging messages over a public channel. † NTT Communication Science Laboratories.
For example, if an algorithm works using a key that is a string of 10 bits, then its key space is the set of all binary strings of length 10 bits; i.e. we have key space of size 210 = 1024. To avoid attackers from guessing the key using a brute-force attack, the key space is usually designed to be very large.
Using data in a database as an example, while the data is stored in the database, it is encrypted with the symmetric key. Once an authorized user attempts to access the data, the information is decrypted with the same symmetric key and made accessible to the user.
Diffie-Hellman is an example of a key agreement protocol. In Diffie-Hellman, each party generates a public keypair and shares their public key with the other person. By combining their own private key with the other party's public key, they produce the same secret key, which can be used for symmetric encryption.
Key agreement refers to one form of key exchange (see also key encryption key) in which two or more users execute a protocol to securely share a resultant key value. As an alternative to key agreement, a key transport protocol may be used.
Key Employee agrees to serve Employer faithfully and to the best of Key Employee's ability and to devote Key Employee's full time, attention and efforts to the business and affairs of Employer during the term of Key Employee's employment.
Key employee determination Key employees are defined as the following: 5% owners (own more than 5%) 1% owners (own more than 1%) with salary in excess of $150,000. Officers with annual salary in excess of $130,000, as indexed ($220,000 for 2024)
Key employee examples are the chief executive officer (CEO), chief operating officer (COO), sales managers, innovators, such as the heads of research and development, and specialists, such as data scientists, quants, or lawyers.