Revokes Dies Ways With The Users
Description
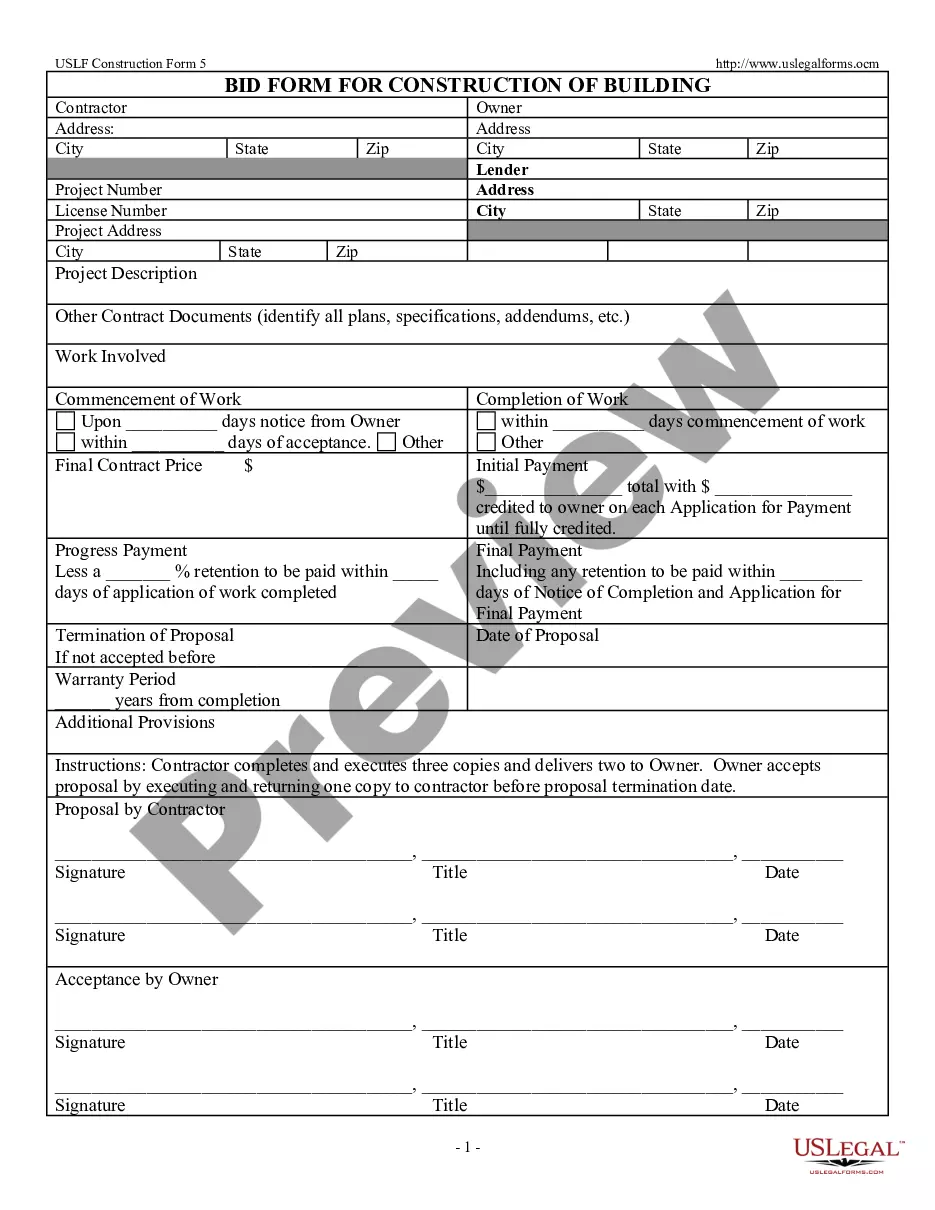
How to fill out Missouri TOD - Transfer On Death Deed Or Beneficiary Deed - Husband And Wife To Four Individuals?
- Log in to your US Legal Forms account if you're a returning user, and verify that your subscription is active. Download the template you need by clicking the Download button.
- For new users, begin by browsing through the preview mode and detailed form descriptions to confirm you select the correct document that aligns with your local legal requirements.
- If the selected template does not meet your needs, utilize the Search function at the top of the page to find an appropriate alternative.
- Once you've found the right document, click the Buy Now button and select your desired subscription plan. You will need to create an account to gain full access.
- Complete your purchase by entering your payment information, such as credit card or PayPal details.
- Download the form you purchased and save it to your device. You can also access it anytime later from the 'My Forms' menu in your account.
By utilizing US Legal Forms, you gain quick access to a robust collection of over 85,000 legal templates, ensuring you find precisely what you need. Additionally, assistance from premium experts is available to guarantee your documents are both accurate and legally sound.
Start simplifying your legal documentation process today by exploring US Legal Forms now!
Form popularity
FAQ
Yes, you can sync two Google Drive accounts using desktop applications or third-party software designed for file synchronization. Setting this up allows you to have files updated across both accounts automatically, which revokes dies ways with the users and enhances your productivity. By using U.S. Legal Forms, you can find the right tools to meet your syncing needs and streamline your file management.
Moving Google Drive files from one account to another requires sharing the files with the second account and making copies there. This ensures that you retain the original files in the first account while the new copies exist in the second one, effectively revokes dies ways with the users. Additionally, tools that facilitate migration can make this process faster and more efficient.
To transfer files between Google Drive accounts, you should first share the files from one account to the other. After sharing, log into the second account, and make a copy of those files to complete the transfer. This process revokes dies ways with the users by ensuring you keep everything organized and in one place without hassle.
You can share Google Drive storage by using the 'Share' feature on the files or folders you want to share. Simply right-click on the item, select 'Share', then enter the email address of the other account. This act not only revokes dies ways with the users, allowing seamless collaboration, but also ensures that both accounts can access the same resources effectively.
To mass transfer Google Drive files, start by selecting multiple files or folders. Then, you can use the 'Download' option to save them to your computer, and subsequently upload them to another account. This method effectively revokes dies ways with the users by simplifying file management between accounts. For an even smoother process, consider using a third-party tool that can automate this bulk transfer.
A will that is 20 years old may still be valid, but several factors come into play. It's crucial to consider whether the terms of the will reflect your current intentions or if changes in your circumstances require updates. Revokes dies ways with the users of outdated documents may lead to complications in estate distribution. To ensure your wishes are honored, consult with a legal expert or utilize platforms like USLegalForms, which provide resources to create or revise your will effectively.
Different types of revocation exist to address various legal scenarios, including complete revocation, partial revocation, and conditional revocation. Complete revocation cancels the entire will, while partial revocation modifies specific parts of it, perhaps excluding certain beneficiaries. Conditional revocation occurs under specific circumstances, such as if a certain event happens—like marriage or divorce—in which the will's terms change automatically. Understanding these options helps in finding effective revokes dies ways with the users.
An example of revocation of a will could involve an individual who decides to marry after previously drafting their will. Upon getting married, they may want to ensure that their new spouse is included as a beneficiary. To do this, they could create a new will that specifically outlines their wishes and includes the revocation of the older will. This transition effectively illustrates the importance of using revokes dies ways with the users to keep your estate plan current.
A will can be revoked in various ways, including physically destroying the original document, creating a new will, or having a formal revocation declaration. Physically destroying the document usually means tearing it up or burning it, signifying the desire to cancel it. Meanwhile, drafting a new will that includes a statement revoking all previous wills serves as a clear declaration of your updated wishes. It's essential to navigate these methods carefully to ensure effective revokes dies ways with the users.
There are three distinct types of revocation that you should know about: explicit revocation, implicit revocation, and revocation by operation of law. Explicit revocation occurs when a person clearly states their intention to cancel a will. Implicit revocation happens when a new will is created that contradicts the previous document. Lastly, revocation by operation of law can occur in specific situations, such as divorce, which renders a spouse as a beneficiary invalid. Understanding these types helps you choose effective revokes dies ways with the users.