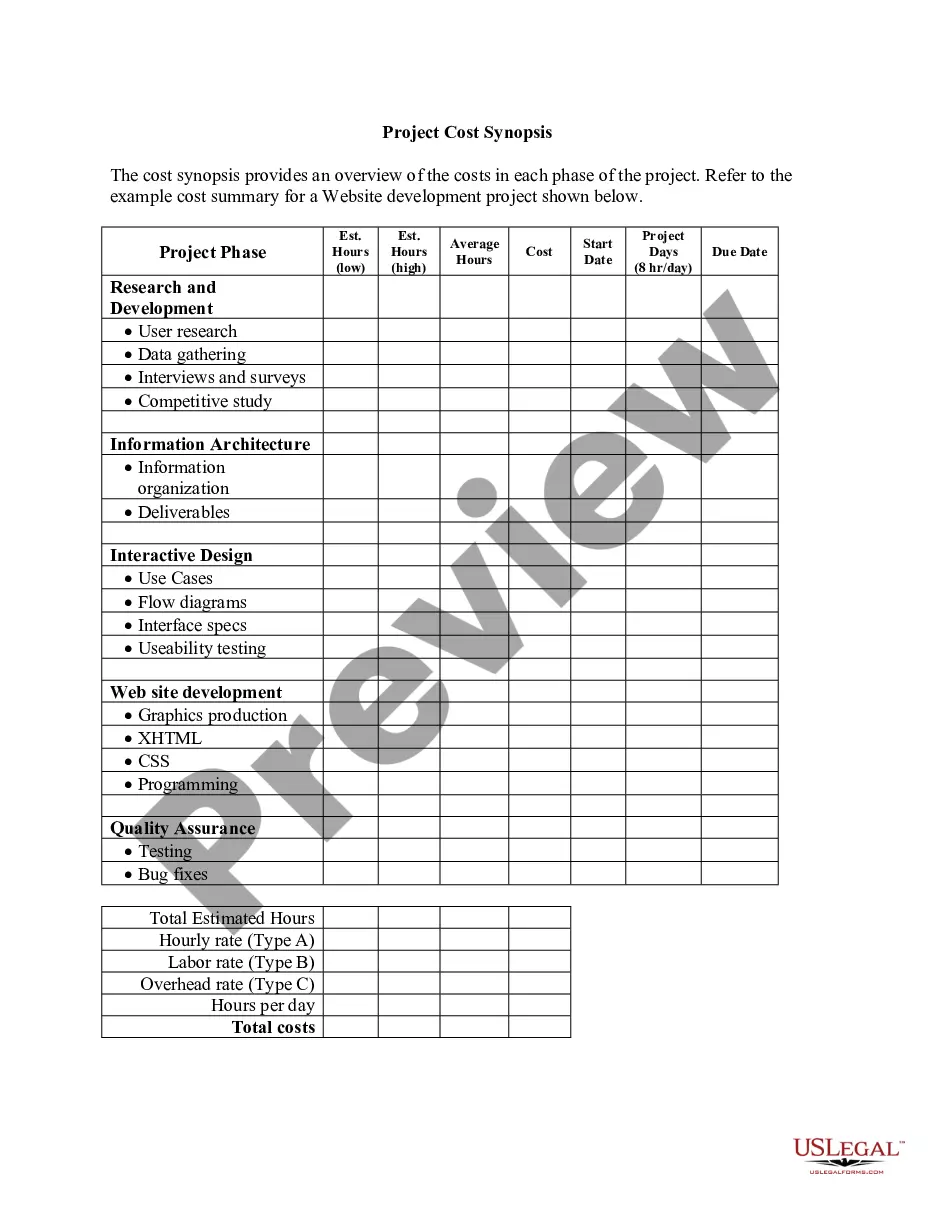
Fort Worth Texas Source Code Security and Purchase Option Agreement
Category:
State:
Multi-State
City:
Fort Worth
Control #:
US-KWP-0008
Format:
Word;
Rich Text
Instant download
Description
This form is a Source Code Security and Purchase Option Agreement. The agreement provides that the first party desires to receive and hold in its possession as security a particular source code. The second party is willing to allow the first party to hold the source code as security and grant the first party an option to purchase the source code under the conditions listed in the agreement.
Free preview