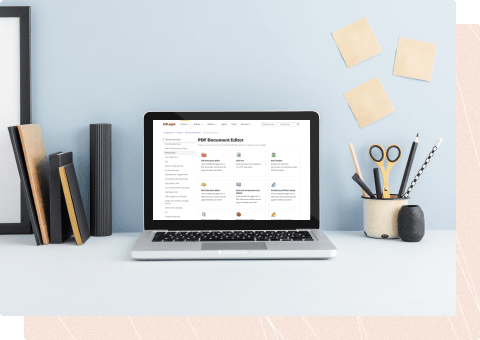
Exploit Comment Document For Free
-
01Upload a document
-
02Edit and fill it out
-
03Sign and execute it
-
04Save and share it or print it out
How to Use the Exploit Comment Document For Free
Exploit Comment Document For Free FAQ
What is an exploit versus a vulnerability?
What is an example of a cybersecurity exploit?
Is it safe to use Google Docs?
What is the vulnerability of Google Docs?
How does Google Docs comment exploit allows for distribution of phishing and malware?
What is an exploit in cyber security?
What's the difference between an exploit and an attack?
What is an example of exploit?
Sign up and try for free!
US Legal Forms fulfills industry-leading security and compliance standards.
-

VeriSign Secured
#1 Internet-trusted security seal. Ensures that a website is free of malware attacks.
-
Accredited Business
Guarantees that a business meets BBB accreditation standards in the US and Canada.
-

TopTen Reviews
Highest customer reviews on one of the most highly-trusted product review platforms.