Loading
Get Key Log 2020-2026
How it works
-
Open form follow the instructions
-
Easily sign the form with your finger
-
Send filled & signed form or save
How to fill out the Key Log online
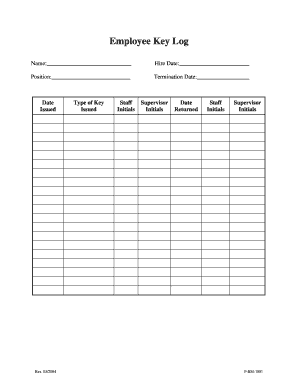
Filling out the Key Log is an essential step for managing access to resources in your workplace. This guide will provide you with clear instructions on how to complete the Key Log accurately and efficiently.
Follow the steps to complete the Key Log online.
- Press the 'Get Form' button to acquire the Key Log. This will allow you to open the document and access all required fields.
- Begin by entering the name of the person receiving the key in the 'Name' field. Ensure that this entry is accurate and complete.
- Next, input the 'Hire Date' to specify when the individual joined the organization. Use the correct date format to avoid confusion.
- In the 'Position' field, indicate the role of the person receiving the key. This helps to clarify their responsibility related to the access provided.
- If applicable, fill in the 'Termination Date' to document the date the person will no longer require access. Leave this blank if not relevant.
- As you issue keys, input the date they are provided under 'Date Issued.' This records when access is granted.
- In the 'Type of Key Issued' section, specify what type of key is being issued, ensuring it matches the access intended.
- Staff members should sign their initials in the appropriate 'Staff Initials' field, indicating they have received the key.
- Supervisors must also initial in the 'Supervisor Initials' field to confirm the issuance of the key.
- When the key is returned, record the 'Date Returned,' updating the status of the key issuance.
- Similar to the issuance process, have both the staff and the supervisor sign their initials in the respective fields upon return.
- Once all the fields are accurately filled out, you can proceed to save your changes, download, print, or share the completed Key Log as necessary.
Complete your Key Log online today and enhance your document management process.
Capturing keystrokes is illegal in many cases, especially if done without the consent of the user. For instance, using a keylogger to secretly monitor someone's activity can lead to serious legal repercussions. However, organizations may lawfully track keystrokes on company devices if employees are informed and agree to such monitoring. An informed approach ensures compliance with laws surrounding keystroke tracking.
Industry-leading security and compliance
US Legal Forms protects your data by complying with industry-specific security standards.
-
In businnes since 199725+ years providing professional legal documents.
-
Accredited businessGuarantees that a business meets BBB accreditation standards in the US and Canada.
-
Secured by BraintreeValidated Level 1 PCI DSS compliant payment gateway that accepts most major credit and debit card brands from across the globe.


