Loading
Get Security Incident Report
How it works
-
Open form follow the instructions
-
Easily sign the form with your finger
-
Send filled & signed form or save
How to fill out the Security Incident Report online
Filing a Security Incident Report is a crucial step in maintaining cyber security. This guide provides a step-by-step approach to help users fill out the form online accurately and efficiently.
Follow the steps to complete your Security Incident Report online effectively.
- Click ‘Get Form’ button to obtain the form and access it in the online platform.
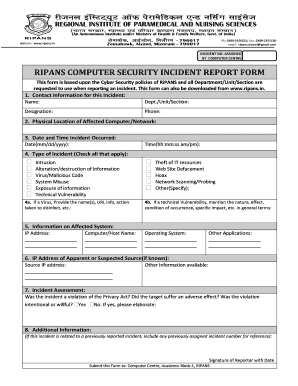
- Provide your contact information for this incident. Fill in your name, department/unit/section, designation, and phone number.
- Identify the physical location of the affected computer or network. Be specific about where the incident took place.
- Record the date and time the incident occurred. Use the format mm/dd/yyyy for the date and hh:mm:ss am/pm for the time.
- Select the type of incident by checking all that apply. Options include intrusion, alteration/destruction of information, virus/malicious code, system misuse, exposure of information, technical vulnerability, theft of IT resources, website defacement, hoax, and network scanning/probing. If applicable, use the provided space to specify details about the incident.
- If applicable, provide details for any virus involved, including the name(s), URL info, and any actions taken to disinfect the system.
- Provide information on the affected system, including the IP address, computer/host name, operating system, and any other applications involved.
- If known, include the IP address of the apparent or suspected source. Also, provide any other related information that might help in assessing the incident.
- Assess the incident by answering whether it violated the Privacy Act, if the target suffered an adverse effect, and whether the violation was intentional or willful. Provide clarification if necessary.
- Add any additional information relevant to the incident, especially if it's related to a previously reported incident. Include the previously assigned incident number for reference.
- Sign the report with your name and date it appropriately. Once completed, submit this form to the Computer Centre, Academic Block-1, RIPANS.
Start filling out your Security Incident Report online today.
Incident reporting allows an organisation to prove that they take security seriously and demonstrate mitigative actions taken. A reporting system should allow an organisation to take the details of a suspected breach and then output these to generate a report if a breach notification is required.
Industry-leading security and compliance
US Legal Forms protects your data by complying with industry-specific security standards.
-
In businnes since 199725+ years providing professional legal documents.
-
Accredited businessGuarantees that a business meets BBB accreditation standards in the US and Canada.
-
Secured by BraintreeValidated Level 1 PCI DSS compliant payment gateway that accepts most major credit and debit card brands from across the globe.


