Loading
Get Nciipc Incident Report Form
How it works
-
Open form follow the instructions
-
Easily sign the form with your finger
-
Send filled & signed form or save
How to fill out the NCIIPC Incident Report Form online
This guide provides a clear and comprehensive approach to filling out the NCIIPC Incident Report Form online. By following the outlined steps, users can ensure that they complete the form accurately and efficiently.
Follow the steps to fill out the form effectively.
- Press the ‘Get Form’ button to access the form and open it in your editor.
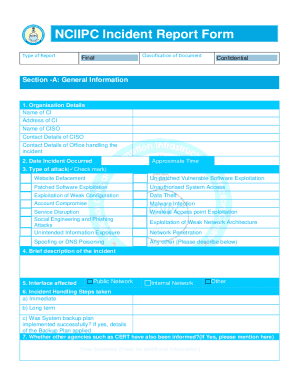
- Begin with Section A: General Information. Enter the name and address of the Critical Infrastructure (CI) along with the name and contact details of the Chief Information Security Officer (CISO) and the office managing the incident.
- Next, specify the date and approximate time the incident occurred to provide a timeline of events.
- Select the type of attack from the provided options by checking the corresponding box. Ensure that you explore all attack types relevant to the incident.
- In the provided space, write a brief description of the incident. Be concise but include all essential details.
- Indicate which interface was affected. Options include Public Network, Internal Network, or Other, depending on the specifics of the incident.
- Detail the incident handling steps taken. Consider immediate actions, long-term strategies, and if a system backup plan was successfully implemented, provide those details.
- Specify if other agencies, such as CERT, have been informed about the incident. If so, mention them in the designated section.
- Identify the impact of the incident on Critical Information Infrastructures (CII) assets by checking all that apply.
- List the number of users affected by the incident to quantify its impact.
- Document the duration of the incident, including the start and end date and time.
- Explain the impact on dependent ICT systems as needed.
- Provide the threat profile including the attacking IP address and source port of the attacking machine.
- Check the type of attack again from the options provided to ensure accurate categorization.
- Conduct a root cause analysis by documenting available reports. If any reports are not available, indicate this clearly.
- Describe the current status of the incident and provide additional details on a separate sheet if necessary.
- Discuss whether a Crisis Management Plan was offered. Provide a detailed explanation as required.
- Once all sections are completed, review the form for accuracy. You can then save changes, and download, print, or share the completed form.
Complete your NCIIPC Incident Report Form online today for thorough documentation and effective incident management.
Incident reports should be completed immediately after a near miss, unexpected, awareness, or adverse events have occurred. This ensures that the involved individuals or witnesses can recall the details of the occurrence with clarity to fill the report form accurately.
Industry-leading security and compliance
US Legal Forms protects your data by complying with industry-specific security standards.
-
In businnes since 199725+ years providing professional legal documents.
-
Accredited businessGuarantees that a business meets BBB accreditation standards in the US and Canada.
-
Secured by BraintreeValidated Level 1 PCI DSS compliant payment gateway that accepts most major credit and debit card brands from across the globe.


