Loading
Get Thank You For Using The Firewall Change Request Form. Please ... - Weill Cornell
How it works
-
Open form follow the instructions
-
Easily sign the form with your finger
-
Send filled & signed form or save
How to use or fill out the Thank You For Using The Firewall Change Request Form. Please ... - Weill Cornell online
Filling out the Firewall Change Request form is an important step in managing your network security needs at Weill Cornell. This guide provides a clear, step-by-step approach to ensure that you complete the form accurately and effectively.
Follow the steps to fill out the form successfully.
- Press the ‘Get Form’ button to obtain the Firewall Change Request form and open it in your preferred editor.
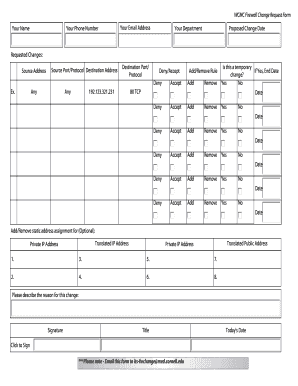
- Begin filling in all necessary sections of the form, starting with your personal demographic information such as name, phone number, email address, and department at the top of the form.
- Identify the section titled 'Requested Changes.' Enter appropriate details such as source address, source port/protocol, destination address, and destination port/protocol based on the changes you wish to request.
- In the section regarding 'Add/Remove Rule,' indicate whether you intend to add or remove a rule for the specified changes. It is essential to indicate if the changes are temporary and, if so, provide an end date.
- Complete the optional 'Add/Remove static address assignment' section if applicable, by providing translated public and private addresses as needed.
- Provide a brief explanation of the reason for the requested change in the designated area.
- Sign the form electronically and include your title in the specified areas.
- Save your completed form. You can also download, print, or share the form as necessary.
- Email the form as an attachment to its-fwchange@med.cornell.edu. No additional information is required in the email body.
- Await a response regarding your request, which should be processed by ITS within 24 hours. You will receive a confirmation of the change or an explanation for any denial.
Start filling out your Firewall Change Request form online today to ensure your network requirements are addressed swiftly.
Prioritizing firewall rules is crucial for managing network security effectively. Generally, you should position rules regarding essential services at the top, while those related to less critical tasks should follow. Thank You For Using The Firewall Change Request Form. Please ... - Weill Cornell aids in determining the best order for your firewall rules.
Industry-leading security and compliance
US Legal Forms protects your data by complying with industry-specific security standards.
-
In businnes since 199725+ years providing professional legal documents.
-
Accredited businessGuarantees that a business meets BBB accreditation standards in the US and Canada.
-
Secured by BraintreeValidated Level 1 PCI DSS compliant payment gateway that accepts most major credit and debit card brands from across the globe.


