Loading
Get Cyber Security Incident Report
How it works
-
Open form follow the instructions
-
Easily sign the form with your finger
-
Send filled & signed form or save
How to fill out the Cyber Security Incident Report online
Completing the Cyber Security Incident Report is crucial for documenting incidents and ensuring appropriate responses. This guide will provide you with clear, step-by-step instructions to fill out the report efficiently and accurately.
Follow the steps to complete the Cyber Security Incident Report online.
- Click 'Get Form' button to access the Cyber Security Incident Report form and open it in the editor.
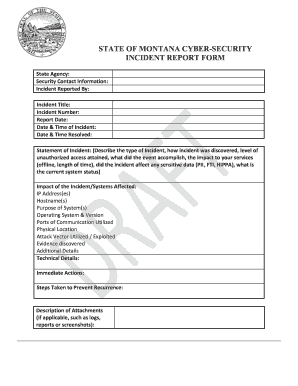
- Begin with the 'State Agency' field. Enter the name of the state agency reporting the incident.
- Fill in the 'Security Contact Information' section with relevant contact details for the individual responsible for security matters within the agency.
- In the 'Incident Reported By' field, enter your name or the name of the person reporting the incident.
- Provide a descriptive 'Incident Title' that summarizes the nature of the incident.
- Enter the 'Incident Number' if applicable, identifying the specific incident.
- Fill in the 'Report Date' with the date of submission for this report.
- Provide the 'Date & Time of Incident' when the incident first occurred.
- Enter the 'Date & Time Resolved' if the incident has been resolved. If not, leave this blank.
- In the 'Statement of Incident,' describe the incident, how it was discovered, the level of unauthorized access attained, its impact on services, sensitive data affected, and the current system status.
- Address the 'Impact of the Incident/Systems Affected' section by specifying the IP address(es), hostname(s), purpose of the system(s), operating system and version, ports of communication utilized, physical location, and attack vector utilized.
- Document any evidence discovered in the 'Evidence discovered' section.
- Use the 'Additional Details' portion to add any relevant context not covered in previous sections.
- In the 'Technical Details' section, provide insights into the incident's technical aspects.
- Complete the 'Immediate Actions' field to outline steps taken in response to the incident.
- List 'Steps Taken to Prevent Recurrence' to indicate measures being implemented to avoid future incidents.
- If applicable, describe any attachments in the 'Description of Attachments' section, such as logs, reports, or screenshots.
- Once all sections are complete, review your entries for accuracy and completeness, then save changes, download, print, or share the form as necessary.
Complete and submit your Cyber Security Incident Report online today to ensure a diligent response to cyber incidents.
A cyber security report is a document that outlines incidents related to computer security breaches or threats. It provides essential information on the nature of the threats encountered, responses, and recommendations for future prevention. Ultimately, a thorough Cyber Security Incident Report is crucial for understanding vulnerabilities and establishing effective security measures.
Industry-leading security and compliance
US Legal Forms protects your data by complying with industry-specific security standards.
-
In businnes since 199725+ years providing professional legal documents.
-
Accredited businessGuarantees that a business meets BBB accreditation standards in the US and Canada.
-
Secured by BraintreeValidated Level 1 PCI DSS compliant payment gateway that accepts most major credit and debit card brands from across the globe.


