Extract Data From Legal Virginia Identity Theft Forms For Free
How it works
-

Import your Virginia Identity Theft Forms from your device or the cloud, or use other available upload options.
-
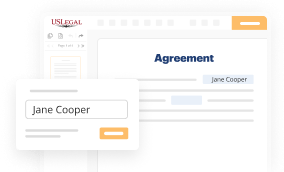
Make all necessary changes in your paperwork — add text, checks or cross marks, images, drawings, and more.
-

Sign your Virginia Identity Theft Forms with a legally-binding electronic signature within clicks.
-
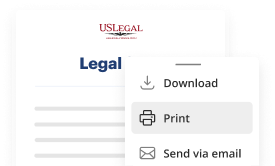
Download your completed work, export it to the cloud, print it out, or share it with others using any available methods.
How to Extract Data From Legal Virginia Identity Theft Forms For Free
Are you tired of constant document printing, scanning, postal delivery, and spending precious time and resources with manual fill-out? The times have moved on, and the easiest way to Extract Data From Legal Virginia Identity Theft Forms For Free and make any other critical adjustments to your forms is by managing them online. Select our quick and trustworthy online editor to fill out, adjust, and execute your legal paperwork with maximum productivity.
Here are the steps you should take to Extract Data From Legal Virginia Identity Theft Forms For Free easily and quickly:
- Upload or import a file to the service. Drag and drop the template to the upload area, import it from the cloud, or use another option (extensive PDF catalog, emails, URLs, or direct form requests).
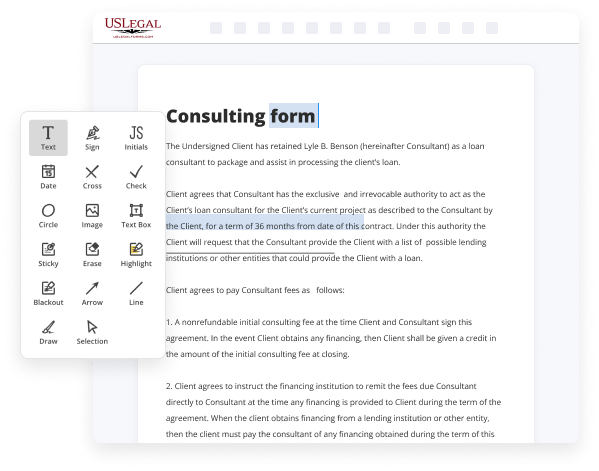
- Provide details you need. Complete empty fields utilizing the Text, Check, and Cross tools from our upper pane. Use our editor’s navigation to make certain you’ve completed everything. Accentuate the most important details with the Highlight option and erase or blackout areas with no value.
- Adjust and rearrange the form. Use our upper and side toolbars to update your content, drop extra fillable fields for various data types, re-order pages, add new ones, or delete redundant ones.
- Sign and collect signatures. Whatever method you select, your eSignature will be legally binding and court-admissible. Send your form to others for signing using email or signing links. Notarize the document right in our editor if it needs witnessing.
- Share and save the copy. Download or export your completed paperwork to the cloud in the file format you need, print it out if you require a hard copy, and choose the most appropriate file-sharing method (email, fax, SMS, or delivered by snail mail using the USPS).
With our service, you don’t have any more excuses to complete legal documents manually. Save time and effort executing them online twice as fast and more properly. Try it out now!

Benefits of Editing Virginia Identity Theft Forms Online
Top Questions and Answers
Credit Card Offers, Bank Statements, Canceled Checks, and More Documents Containing Financial Information. An identity thief could potentially use anything that comes from a financial institution. ... Documents Containing Personal Information. ... Documents Containing Account Information. ... Junk Mail. ... Child- and School-Related Mail.
Related Features
Tips to Extract Data From Legal Virginia Identity Theft Forms For Free
- Carefully read the instructions on the legal Virginia identity theft forms to understand what information is required.
- Gather all necessary documents related to the identity theft case, such as police reports and identification cards.
- Ensure all personal information is accurate and matches government records to avoid any discrepancies.
- Use clear and concise language when filling out the forms to make the data easy to read.
- Check for any specific formatting guidelines mentioned in the form, such as date formats or signature requirements.
- Double-check all entries for typos or missing information before submitting the forms.
- Keep copies of all submitted forms and supporting documents for your records.
- Consider seeking help from a legal professional if you are unsure about any part of the process.
This editing feature for extracting data from legal Virginia identity theft forms may be needed if you are assisting someone who is a victim of identity theft or if you need to correct any mistakes in the initial submission.
Related Searches
Rather than completing several different forms, you can use the Identity Theft Affidavit to alert businesses about the fraud. The company can then investigate ... A copy of your FTC Identity Theft Report; A government-issued ID with a photo; Proof of your address (mortgage statement, rental agreement, or ... Visit the eForms page and click on the form you were preparing. A pop-up titled "Retrieve Saved Data" will appear. Enter your password to continue working on ... For purposes of this subsection, "facial recognition technology" means an electronic system for enrolling, capturing, extracting, comparing, and matching an ... An Entity shall disclose the breach of the security of the system if encrypted information is accessed and acquired in an unencrypted form, or if the security ... Shred or destroy papers containing your personal information including credit card offers and ?convenience checks? you don't use. Remember that Dumpster-diving ... ID theft is when someone illegally poses as you, usually to get money. Know these warning signs and prevention tips. By filing your identity theft complaint with the Federal Trade Commission, you will provide important information that can help law enforcement track down ... Tax-related identity theft happens when someone steals your personal information to commit tax fraud. ... An error occurred while retrieving sharing information. Steal your wallet or purse to get ID, credit, or bank cards; Go through your trash to retrieve bank statements or tax documents; Install ...
Industry-leading security and compliance
-
In businnes since 1997Over 25 years providing professional legal documents.
-
Accredited businessGuarantees that a business meets BBB accreditation standards in the US and Canada.
-
Secured by BraintreeValidated Level 1 PCI DSS compliant payment gateway that accepts most major credit and debit card brands from across the globe.
-
VeriSign secured#1 Internet-trusted security seal. Ensures that a website is free of malware attacks.