Extract Data From Electronic Identity Theft Templates For Free
How it works
-

Import your Identity Theft Forms from your device or the cloud, or use other available upload options.
-
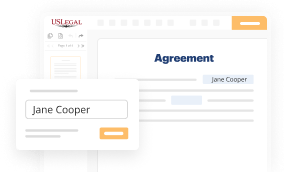
Make all necessary changes in your paperwork — add text, checks or cross marks, images, drawings, and more.
-

Sign your Identity Theft Forms with a legally-binding electronic signature within clicks.
-
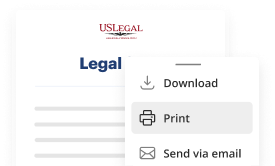
Download your completed work, export it to the cloud, print it out, or share it with others using any available methods.
How to Extract Data From Electronic Identity Theft Templates For Free
Web-based document editors have demonstrated their reliability and efficiency for executing legal documents. Utilize our secure, rapid, and user-friendly service to Extract Data From Electronic Identity Theft Templates For Free your files whenever necessary, with minimal effort and utmost accuracy.
And that’s how you can finalize and distribute any personal or business legal documentation in just a few clicks. Give it a try now!
- Import a document into the editor. You can choose from several options - upload it from your device or the cloud, or import it from a form catalog, external URL, or email attachment.
- Complete the blank fields. Place the cursor on the first unfilled field and use our editor’s navigation to progress step-by-step to ensure nothing is overlooked on your template. Utilize Text, Initials, Cross, and Check functionalities.
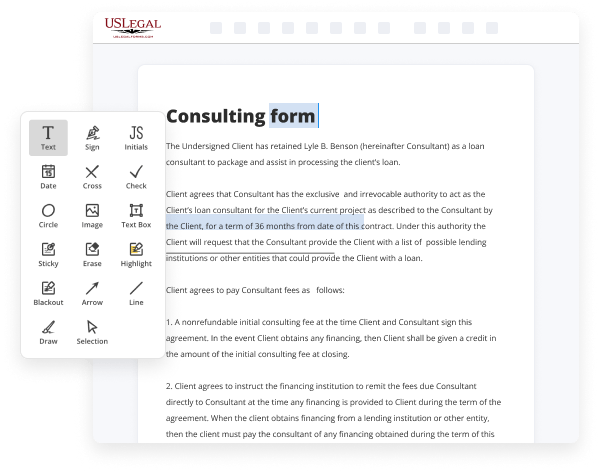
- Make the necessary adjustments. Update the document with added images, draw lines and icons, emphasize important elements, or eliminate any unnecessary ones.
- Create additional fillable areas. Alter the template by adding a new section for filling out if needed. Use the right-side tool panel for this, drop each field where you expect others to submit their data, and set the remaining areas as required, optional, or conditional.
- Arrange your pages. Delete pages you no longer need or create new ones using the appropriate button, rotate them, or change their sequence.
- Generate eSignatures. Click on the Sign option and select how you’d like to add your signature to the document - by typing your name, drawing it, uploading its image, or using a QR code.
- Share and send for eSigning. Conclude your editing with the Done button and send your copy to others for signing via an email request, with a Link to Fill option, in an SMS or fax message. Request a swift online notarization if needed.
- Save the document in the format you require. Download your paperwork, store it in cloud storage in its current format, or convert it as needed.

Benefits of Editing Identity Theft Forms Online
Top Questions and Answers
The most common outcome of identity theft is financial loss, which can affect your credit score and financial stability. Victims frequently face challenges with unauthorized charges or loans taken out in their name. Fortunately, accessing resources that extract data from electronic identity theft templates can simplify the recovery process. These tools provide you with necessary information to navigate the aftermath effectively.
Tips to Extract Data From Electronic Identity Theft Templates For Free
- 1. Use a reliable data extraction tool or software that is specifically designed for extracting data from electronic identity theft templates.
- 2. Make sure to carefully review the template before extracting any data to ensure accuracy and completeness.
- 3. Utilize advanced search and filter options to extract specific data fields or information from the template.
- 4. Consider setting up automated extraction processes to save time and reduce manual errors.
- 5. Keep the extracted data secure by using encryption or password protection measures.
- 6. Regularly update your extraction tool to ensure compatibility with new template versions and security updates.
The editing feature for extracting data from electronic identity theft templates may be needed when you need to quickly retrieve important information for an investigation, legal case, or compliance audit. It is important to follow proper data extraction techniques to ensure accuracy and confidentiality of the extracted data.
Related Searches
Extract and verify information from any identity document against external sources - all in real-time. · Document information is extracted from ID document via ... Fill Identity Theft Police Report Template, Edit online. Sign, fax and printable from PC, iPad, tablet or mobile with pdfFiller ? Instantly. Try Now! Use this template to create a generic identity theft Web site to be perpetually published as a public service announcement to your institution's community. Get evidence of the claimed identity. You can collect: physical evidence of the claimed identity (such as an identity document, like a passport) ... We offer a range of solutions that help organisations quickly validate and verify the identity and location of their customers. Correct your personal information. 17. Reduce unwanted sales calls, junk mail and electronic marketing 19. Recognising the signs of identity theft. Identity theft is no longer a theoretical threat. ... biometric system in order to extract biometric data from a biometric source and link. Online ID verification service to help any business, from any industry, collect, verify, and manage user identities throughout a customer lifecycle. Biometric identification consists of determining the identity of a person. The aim is to capture an item of biometric data from this person. It can be a photo ... Identity fraud happens when someone steals and uses your personal information to buy products or services. They get hold of this information in many ways ...
Industry-leading security and compliance
-
In businnes since 1997Over 25 years providing professional legal documents.
-
Accredited businessGuarantees that a business meets BBB accreditation standards in the US and Canada.
-
Secured by BraintreeValidated Level 1 PCI DSS compliant payment gateway that accepts most major credit and debit card brands from across the globe.
-
VeriSign secured#1 Internet-trusted security seal. Ensures that a website is free of malware attacks.